How to Achieve Compliance in the Cloud?
As data privacy becomes a growing concern for the whole society, organizations become much more responsible for securing and protecting the sensitive data in the cloud. While cloud computing revolutionizes the business world, the increased complexity in the cloud environments is bringing new challenges for organizational security and compliance. Organizations need to develop the visibility, control, and predictability in their security practices and compliance processes.
Compliance in the Cloud: How does it differ from On-Prem?
It is important to note that although the dynamic structure of the cloud changes the way of handling data and security, the ultimate goal of compliance is the same: securing the data. However, the difference in cloud compliance is that compliance is now much more a dynamic target for businesses. The pace of compliance standards and their scope increase along with the technological advancements and it becomes harder to follow considering their pace. As the complexity of our infrastructures increases compared to traditional on-premise systems, new ways of thinking and compliance strategies are needed to build a sophisticated security posture.
Cloud compliance, and briefly achieving and maintaining compliance in the cloud requires a proactive approach to compliance management, rather than relatively simpler traditional compliance management in on-prem data centers.
The main areas that cloud compliance differs from on-prem environments are:
- Network Management
In the cloud, your networks are not physical anymore, they are software defined. The management of network configurations, security groups and network access control lists are critical to ensure the security of your networks.
- Infrastructure Management
Compared to the physical environments, cloud computing offers a scalable virtual environment for businesses. Besides its advantages, the virtual environment might become an issue when it comes to managing its security. You should always think about security for the dynamic nature of cloud infrastructures and services.
- Evolving Cybersecurity Landscape
Although it is also applicable to on-prem environments, the evolving and complex cybersecurity threats and risks also bring new challenges for cloud security. Continuous monitoring and effective vulnerability management plans becomes much more important when operating in the cloud.
Achieving Compliance in the Cloud
When designing your compliance strategy, it is important to know your responsibilities, what cloud providers offer for compliance and how to best achieve compliance across your operations.
Shared Responsibility Model
Compliance in the cloud is a bilateral work. As AWS defines, cloud security is a Shared Responsibility between you and the cloud provider. The main idea of the Shared Responsibility Model is that it is both yours and your cloud providers' responsibility to secure your operations, workloads, applications and data in the cloud. Below, there is a Shared Responsibility Model diagram of AWS, where your stack is divided into different pieces based on the compliance responsibilities. When you design your compliance strategy, it is important for you to know who does what to prepare for full compliance.
The Shared Responsibility Model consists of 2 main parts: named as security of the cloud and security in the cloud, where the responsibilities of AWS and businesses are separated and defined.
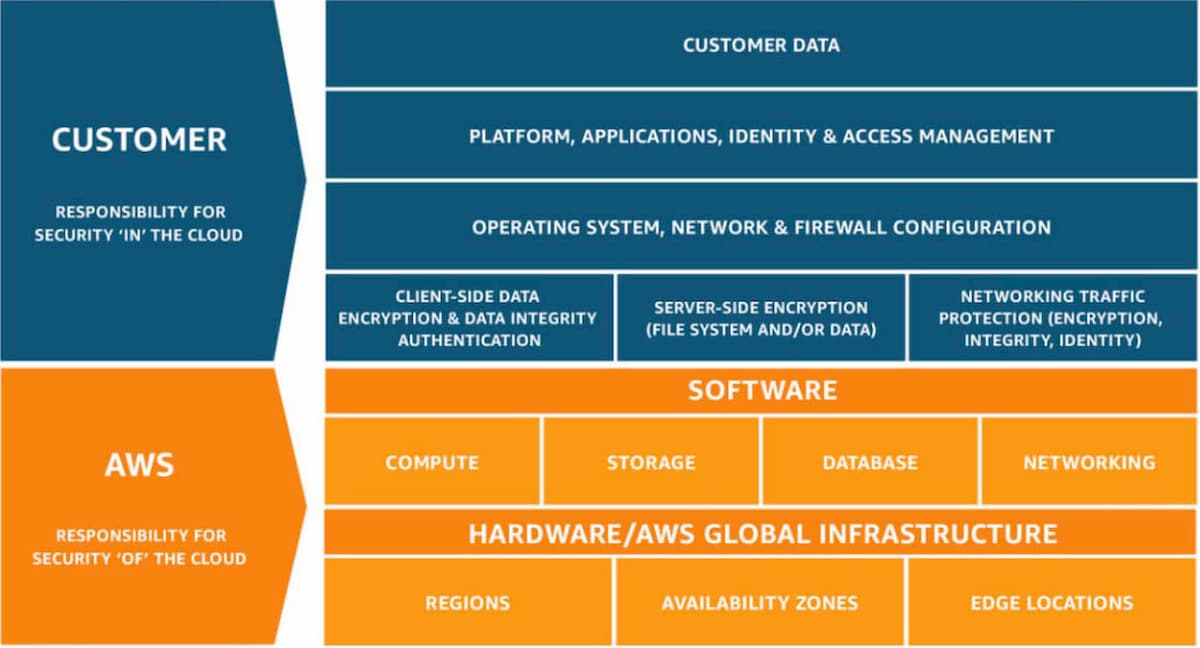
Fig. 1: AWS Shared Responsibility Model1
Starting from the bottom, AWS takes the responsibility of securing the whole infrastructure and services it offers. By this way, businesses don’t have to work on and worry about the physical security of the hardware, network, and hypervisors. AWS also takes the 100% responsibility for securing these elements.
Continuing on the upper part, the customer is 100% responsible for the security of everything they set up, configure, run, own and use in the cloud. It is important to note that AWS has zero visibility in this part. Your operating system, applications, the data you hold, store or archive in the cloud is not known and accessed by AWS.
Now it is time to understand what businesses are responsible for. First of all, securing the guest operating system is the businesses’ responsibility. For example, you should configure, manage and check the security updates and patches for your instances if you are running your applications on EC2. Additionally, securing and protecting the applications you run on your cloud environment and the data you hold in the cloud are totally your responsibility. This includes securing the network traffic, implementing data encryption, enforcing access security methods across your organization using MFA and IAM principles and such. Overall, the Shared Responsibility Model helps customers take a lot of burden off their shoulders with the built-in security in the cloud.
Implementing Security by Design
Standardizing the way you build, analyze, report and manage your infrastructure and implementing a systematic approach can help you achieve compliance in the cloud. Security by Design principles in AWS help improve and gain consistency in your security practices across all IT infrastructure and cloud resources through standardization, automation and repetition of specified security standards. You can leverage SbD templates with AWS CloudFormation and implement a systematic approach to follow specified security practices and reduce complexity when you deploy changes on your infrastructure.
Security by Design approach is applicable to your cloud infrastructure in every aspect: you can automate the security practices and compliance processes within your account structure and achieve the desired level of security as you operate. The prescriptive nature of Security by Design principles including all cloud operations from permissions to configuration management, help you follow compliance requirements continuously and consistently across your organization
Security by Design theory can be described as:
-
Standardizing your AWS account design: Creating templates, runbooks, procedures, incident management policies helps you effectively secure your infrastructure in your chosen way and supports compliance processes in terms of audits and documentation.
-
Automating Security Controls: Having full visibility and control over your infrastructure helps you detect any suspicious activity, whether it comes from external sources or just occurs due to unintentional internal mistakes.
-
Streamlining auditing: These Security by Design principles in templates also ease your compliance audit processes through centralized management and documentation.
Considering the complexity of your cloud infrastructure, you can streamline your compliance management with embracing Security by Design on AWS. By this way, every cloud operation becomes aligned with your compliance strategy.
Power of Tooling: AWS Services to Ease Your Compliance Process
AWS Artifact
First things first, let’s start with AWS Artifact, the service that provides various compliance reports that AWS has. When the reports on security of physical infrastructure and networks are asked by your compliance auditors, you can simply get these reports and related documentation from AWS with AWS Artifact.
Amazon Inspector
Amazon Inspector is a vulnerability and threat scanning service for your EC2 instances. It is simply an EC2 agent, monitoring incoming and outgoing traffic through the instances. Amazon Inspector offers pre-built templates for various compliance requirements and benchmarks. With using tags on Amazon Inspector, you can easily scan your instances through different templates for compliance standards. Amazon Inspector provides reports for the instance scans and you can use these reports for both internal monitoring and compliance audit documentations.
Amazon WAF
Amazon WAF reduces the vulnerability for evolving web attacks by enabling you to create access rules for your applications 24/7. You can leverage AWS WAF in your development processes as well to ensure embedded and continuous security. You can put AWS WAF in front of Cloudfront distributions and create your set of rules to define the traffic you want to allow based on your compliance requirements. AWS WAF provides a centralized management for web application protection and continuous visibility to achieve strong security and compliance.
Amazon Detective
Amazon Detective is a service to identify and manage potential security issues and suspicious events. It helps businesses analyze, investigate and take action against potential security events with collecting log data from AWS resources and provides insights from the data using ML and various analysis methods. Easier root cause analysis and identification help businesses improve their security posture and support compliance processes.
Amazon Macie
Amazon Macie is a service that leverages ML to scan your data across S3 buckets and recognize the sensitive data that should be protected. Amazon Macie automates the management of sensitive data across your cloud environment and helps you implement required levels of protection against sensitive data with alert mechanisms. Such alerts can be triggered by unencrypted data, poor access level permissions or any given insufficient protection method.
Of course, the security and compliance enabling AWS services are not limited with the ones listed above. You can implement continuous security monitoring, vulnerability management and built-in security features across your cloud environment with various AWS services.

- AWS Shared Responsibility Model https://aws.amazon.com/compliance/shared-responsibility-model↩
About the Author:
Deniz Güreler
Growth Specialist
A fresh new graduate and specializing in marketing, Deniz is excited to learn and share her knowledge on business technologies and technology culture. With her experience in technology companies during her school years, she is always excited to learn more about how technology transforms businesses.
Start Your Digital Transformation
Book an Appointment
Subscribe to Our Newsletter
Our Service
Specialties

Copyright © 2018-2025 Sufle
We use cookies to offer you a better experience with personalized content.
Cookies are small files that are sent to and stored in your computer by the websites you visit. Next time you visit the site, your browser will read the cookie and relay the information back to the website or element that originally set the cookie.
Cookies allow us to recognize you automatically whenever you visit our site so that we can personalize your experience and provide you with better service.